GlobalVoices: China: Be aware! Google Earth leaks national secret
On May 6, famous blogger, William Long, was summoned by the Shenzhen Urban Planning and Land Supervision Division that a Google Earth picture indicating military facilities at www.moon-bbs.com is in suspect of leaking national secret. During the conversation, someone recorded the whole process with video.
Ogle Earth: China cracks down on user-generated maps
Having lived in China for just over a year, I've seen the progressive blocking of Facebook, Twitter, Blogspot, YouTube and now most recently DropBox, so today should not have come as a surprise: User-generated maps and annotations are up next.
danwei: Dodgy CCTV journalism and map clampdown
The CCTV program 'Topics in Focus', ever happy to attack Internet companies, especially Google, participated in the purge by airing a program last night showing how a Chinese blogger was "revealing state secrets" by writing annotations on Google Earth.
South China Morning Post: Censored: the map website accused of leaking site of PLA HK barracks
"Everyone can freely mark information about buildings, even the houses of some top leaders and other so-called secrets, and share them at Google Earth; that's why they want to control such behaviour," he said.
Wednesday, May 19, 2010
Sunday, July 5, 2009
Top Ten Open Source PHP Apps
Open-source PHP applications that changed the world. From managing databases to shopping, writing blogs to sending emails. Ten years of passion, great software architectures, team work and revolutionary ideas. Here are the most influential open-source PHP applications.
Blog
Wordpress - is a state-of-the-art semantic personal publishing platform with a focus on aesthetics, web standards, and usability.
BBS
phpBB -is a high powered, fully scalable, and highly customizable open-source bulletin board package. phpBB has a user-friendly interface, simple and straightforward administration panel, and helpful FAQ. Based on the powerful PHP server language and your choice of MySQL, MS-SQL, PostgreSQL or Access/ODBC database servers, phpBB is the ideal free community solution for all web sites. Features include: Unlimited forums and posts; Multiple language interface; Private or public forums; Powerful search utility; Private messaging system; Templates.
CMS
Drupal - an open source content management platform. Equipped with a powerful blend of features, Drupal supports a variety of websites ranging from personal weblogs to large community-driven websites.
Wikis
MediaWiki - is a free software wiki package originally written for Wikipedia. It allows collaborative editing on documents within a familiar interface. It was designed to be run on a large server farm and requires Apache, PHP, and MySQL.
Database Tools
phpMyAdmin - handles the administration of MySQL over the Web. phpMyAdmin performs many database administration tasks like running SQL statements, adding and dropping databases, and adding, editing or deleting tables or fields.
Photo Tools
Gallery - is an open source project with the goal to develop and support leading photo sharing web application solutions. It allow some basic photo manipulation, such as resizing, rotating, and altering image quality, but does not include advanced photo editing.
Advertising Tools
OpenX - OpenX is a hugely popular, free ad server for web publishers. Take control, manage your advertising and make more money from online advertising today.
DIGG
Pligg - Pligg CMS provides free software to create your own social networking website. Start a site in minutes using Pligg Content Management System and save time and money on your next website.
RSS
Gregarius–Gregarius is a web-based RSS/RDF/ATOM feed aggregator, designed to run on your web server, allowing you to access your news sources from wherever you want.
E-Commerce
osCommerce - osCommerce("open source Commerce") is an e-commerce and online store-management software program. It can be used on any web server that has PHP and MySQL installed. osCommerce provides a basic set of functionality that meets the common needs of online businesses.
Blog
Wordpress - is a state-of-the-art semantic personal publishing platform with a focus on aesthetics, web standards, and usability.
BBS
phpBB -is a high powered, fully scalable, and highly customizable open-source bulletin board package. phpBB has a user-friendly interface, simple and straightforward administration panel, and helpful FAQ. Based on the powerful PHP server language and your choice of MySQL, MS-SQL, PostgreSQL or Access/ODBC database servers, phpBB is the ideal free community solution for all web sites. Features include: Unlimited forums and posts; Multiple language interface; Private or public forums; Powerful search utility; Private messaging system; Templates.
CMS
Drupal - an open source content management platform. Equipped with a powerful blend of features, Drupal supports a variety of websites ranging from personal weblogs to large community-driven websites.
Wikis
MediaWiki - is a free software wiki package originally written for Wikipedia. It allows collaborative editing on documents within a familiar interface. It was designed to be run on a large server farm and requires Apache, PHP, and MySQL.
Database Tools
phpMyAdmin - handles the administration of MySQL over the Web. phpMyAdmin performs many database administration tasks like running SQL statements, adding and dropping databases, and adding, editing or deleting tables or fields.
Photo Tools
Gallery - is an open source project with the goal to develop and support leading photo sharing web application solutions. It allow some basic photo manipulation, such as resizing, rotating, and altering image quality, but does not include advanced photo editing.
Advertising Tools
OpenX - OpenX is a hugely popular, free ad server for web publishers. Take control, manage your advertising and make more money from online advertising today.
DIGG
Pligg - Pligg CMS provides free software to create your own social networking website. Start a site in minutes using Pligg Content Management System and save time and money on your next website.
RSS
Gregarius–Gregarius is a web-based RSS/RDF/ATOM feed aggregator, designed to run on your web server, allowing you to access your news sources from wherever you want.
E-Commerce
osCommerce - osCommerce("open source Commerce") is an e-commerce and online store-management software program. It can be used on any web server that has PHP and MySQL installed. osCommerce provides a basic set of functionality that meets the common needs of online businesses.
Saturday, January 31, 2009
Google Search Results in Warning Entire Internet
Today, some searchers found every site in Google's search results carried the warning that: "This site may harm your computer". Users who attempted to click through the results saw the "interstitial" warning page that mentions the possibility of badware and refers people to StopBadware.org for more information.
The problem affected internet pages across the whole planet, and lasted for around 40 minutes before engineeers were able to fix it.
"We periodically receive updates to that list and received one such update to release on the site this morning. Unfortunately (and here's the human error), the URL of '/' was mistakenly checked in as a value to the file and '/' expands to all URLs. Fortunately, our on-call site reliability team found the problem quickly and reverted the file," Google said in its official blog.

The problem affected internet pages across the whole planet, and lasted for around 40 minutes before engineeers were able to fix it.
"We periodically receive updates to that list and received one such update to release on the site this morning. Unfortunately (and here's the human error), the URL of '/' was mistakenly checked in as a value to the file and '/' expands to all URLs. Fortunately, our on-call site reliability team found the problem quickly and reverted the file," Google said in its official blog.

Friday, January 23, 2009
Top Ten Mobile Games in 2008
Nielsen has released their top 10 mobile games for the U.S. operator market in 2008. Not surprisingly, Tetris is still leading the charts with an overall revenue of 7.0%.
1. 7.0% Tetris
2. 4.0% Bejeweled
3. 3.6% Guitar Hero III
4. 2.6% Wheel of Fortune
5. 2.5% Pac-Man
6. 1.9% The Oregon Trail
7. 1.7% Ms. Pac-Man
8. 1.6% Are You Smarter Then...
9. 1.6% Tetris Mania
10. 1.2% Surviving High School
This chart clearly shows the strong value of brands on the U.S. operators decks. The fact that there are two Tetris and Pac-Man related titles says it all. The U.S. consumer did not change in 2008.
1. 7.0% Tetris
2. 4.0% Bejeweled
3. 3.6% Guitar Hero III
4. 2.6% Wheel of Fortune
5. 2.5% Pac-Man
6. 1.9% The Oregon Trail
7. 1.7% Ms. Pac-Man
8. 1.6% Are You Smarter Then...
9. 1.6% Tetris Mania
10. 1.2% Surviving High School
This chart clearly shows the strong value of brands on the U.S. operators decks. The fact that there are two Tetris and Pac-Man related titles says it all. The U.S. consumer did not change in 2008.
Monday, January 19, 2009
Top Ten Best Java Mobile Games
Here i have some of Most Interesting and popular java games for your mobiles. Download ten mobile games for your Nokia, sony ericson, Samsung and Motorola mobiles. Here is the list of some of Top Java Mobile games for your mobile.
Tetris is a puzzle video game that descend from the notion of blocks falling down into pits. Some of those, like Puyo Puyo, are hugely influential in their own right. It's the most-played, most-imitated, most influential puzzler of all time.

Super Bubble Bobble is an arcade game by Taito。 The game features twin Bubble Dragons journey through the Cave of Monsters to rescue their girlfriends. They move over a system of platforms, busting and pushing bubbles, avoiding enemies and collecting a variety of power-ups.

Super Mario Bros is a platform game developed by Nintendo. In Super Mario Bros., the titular character Mario must save Princess Toadstool of the Mushroom Kingdom from the evil King Koopa, king of the Koopas.

Pac-Man is an arcade game developed by Namco. The player controls Pac-Man through a maze, eating pac-dots. When all dots are eaten, Pac-Man is taken to the next stage. Four ghosts (Blinky, Pinky, Inky and Clyde) roam the maze, trying to catch Pac-Man. If a ghost touches Pac-Man, a life is lost. When all lives have been lost, the game ends.
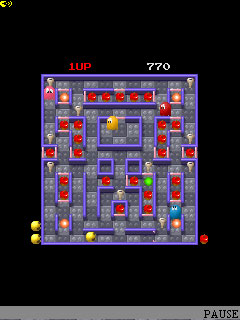
Snake is a video game released during the mid 1970s and has maintained popularity since then, becoming somewhat of a classic. After it became the standard pre-loaded game on Nokia phones in 1998, Snake found a massive audience and soon became the most-played videogame of all time. More than one billion people have played Snake.

Bejeweled is a puzzle game by PopCap Games. The objective of this game is to swap one gem with an adjacent gem to form a horizontal or vertical chain of three or more gems. Bonus points are given when more than three identical gems are formed or forms two lines of identical gems in one swap. Gems disappear when chains are formed and gems fall from the top to fill in gaps. Sometimes chain reactions, called cascades, are triggered, where chains are formed by the falling gems. Cascades are awarded with bonus points.

Zuma is a fast-paced puzzle game developed by PopCap Games. The objective of Zuma is to eliminate all of the balls rolling around the screen along a given path (the path is clearly visible in all of the levels except the last level), before these balls reach the yellow skull structure, which will open to varying degrees as a warning of oncoming balls. As soon as one ball reaches the skull, the rest follow and the player loses a life. To prevent the balls reaching the Skull, the player can eliminate the balls by firing a colored ball from the stone frog idol's mouth towards the chain of balls that will continue to push forward until the player fills the yellow bar, which is when the balls will stop producing off-screen. When three or more of the same color come in contact, they explode, possibly triggering other explosions as part of a chain reaction. The level is completed when after the bar is filled, the player eliminates all of the balls on the screen.

Bomberman is an arcade-style maze-based video game developed by Hudson Soft. Bomberman, is a robot that wants to be free from his job at an underground bomb factory. He must find his way through a maze while avoiding enemies. Doors leading to further maze rooms are found under rocks, which Bomberman must destroy with bombs. There are items that can help improve Bomberman's bombs, such as the Fire ability, which improves the blast range of his bombs. Bomberman will turn human when he escapes and reaches the surface. Each game has 50 levels in total.
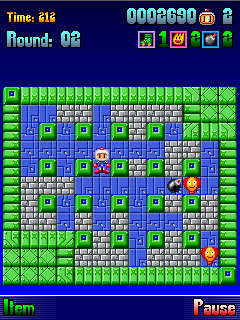
Prince of Persia is an action-adventure video game franchise that was created by Jordan Mechner. In 2007, Prince of Persia was remade and ported by Gameloft. The remake, titled Prince of Persia Classic. It featured the same level design and general premise and gameplay of the original, but contained 3D-rendered graphics, and more fluid movements. New game modes were also added.

The Sims is a strategic life-simulation computer game developed by Maxis and published by Electronic Arts. It is a simulation of the daily activities of one or more virtual persons in a suburban household near SimCity.

The pack includes the following games (resolution: 240x320), click here to download.
Tetris is a puzzle video game that descend from the notion of blocks falling down into pits. Some of those, like Puyo Puyo, are hugely influential in their own right. It's the most-played, most-imitated, most influential puzzler of all time.

Super Bubble Bobble is an arcade game by Taito。 The game features twin Bubble Dragons journey through the Cave of Monsters to rescue their girlfriends. They move over a system of platforms, busting and pushing bubbles, avoiding enemies and collecting a variety of power-ups.

Super Mario Bros is a platform game developed by Nintendo. In Super Mario Bros., the titular character Mario must save Princess Toadstool of the Mushroom Kingdom from the evil King Koopa, king of the Koopas.

Pac-Man is an arcade game developed by Namco. The player controls Pac-Man through a maze, eating pac-dots. When all dots are eaten, Pac-Man is taken to the next stage. Four ghosts (Blinky, Pinky, Inky and Clyde) roam the maze, trying to catch Pac-Man. If a ghost touches Pac-Man, a life is lost. When all lives have been lost, the game ends.

Snake is a video game released during the mid 1970s and has maintained popularity since then, becoming somewhat of a classic. After it became the standard pre-loaded game on Nokia phones in 1998, Snake found a massive audience and soon became the most-played videogame of all time. More than one billion people have played Snake.

Bejeweled is a puzzle game by PopCap Games. The objective of this game is to swap one gem with an adjacent gem to form a horizontal or vertical chain of three or more gems. Bonus points are given when more than three identical gems are formed or forms two lines of identical gems in one swap. Gems disappear when chains are formed and gems fall from the top to fill in gaps. Sometimes chain reactions, called cascades, are triggered, where chains are formed by the falling gems. Cascades are awarded with bonus points.

Zuma is a fast-paced puzzle game developed by PopCap Games. The objective of Zuma is to eliminate all of the balls rolling around the screen along a given path (the path is clearly visible in all of the levels except the last level), before these balls reach the yellow skull structure, which will open to varying degrees as a warning of oncoming balls. As soon as one ball reaches the skull, the rest follow and the player loses a life. To prevent the balls reaching the Skull, the player can eliminate the balls by firing a colored ball from the stone frog idol's mouth towards the chain of balls that will continue to push forward until the player fills the yellow bar, which is when the balls will stop producing off-screen. When three or more of the same color come in contact, they explode, possibly triggering other explosions as part of a chain reaction. The level is completed when after the bar is filled, the player eliminates all of the balls on the screen.

Bomberman is an arcade-style maze-based video game developed by Hudson Soft. Bomberman, is a robot that wants to be free from his job at an underground bomb factory. He must find his way through a maze while avoiding enemies. Doors leading to further maze rooms are found under rocks, which Bomberman must destroy with bombs. There are items that can help improve Bomberman's bombs, such as the Fire ability, which improves the blast range of his bombs. Bomberman will turn human when he escapes and reaches the surface. Each game has 50 levels in total.

Prince of Persia is an action-adventure video game franchise that was created by Jordan Mechner. In 2007, Prince of Persia was remade and ported by Gameloft. The remake, titled Prince of Persia Classic. It featured the same level design and general premise and gameplay of the original, but contained 3D-rendered graphics, and more fluid movements. New game modes were also added.

The Sims is a strategic life-simulation computer game developed by Maxis and published by Electronic Arts. It is a simulation of the daily activities of one or more virtual persons in a suburban household near SimCity.

The pack includes the following games (resolution: 240x320), click here to download.
Thursday, January 1, 2009
Best of Moonlight Blog 2008
As we move into 2009 I thought it might be fun to look back quickly on the year that was with a top 20 post of the most popular posts published on Moonlight Blog this year (according to page views on Google Analytics). I hope you enjoy this trip back through the year of 2008 at Moonlight Blog.
Youtube Unblocked in China - 7,803 views
SourceForge Blocked In China - 7,720 views
Top Ten Best Wordpress Plugins - 5,043 views
Top Ten Best PlayStation Games - 4,812 views
Top Ten Best PS2 Games - 2,822 views
Top Ten Best Firefox Extensions - 2,645 views
WordPress Mod Rewrite Make Subdirectory 404 Error - 2,431 views
Top Ten WordPress SEO Tips - 2,011 views
Google Translation Gadget - 1,899 views
GoDaddy Blocked in China - 1,434 views
WordPress Excerpt Seo Tips - 1,388 views
The Most Popular RSS Reader In China - 1,235 views
Install WordPress MU On IIS With Url Rewrite - 1,225 views
WordPress MU Optimization Script - 1,087 views
Micro-blogging: Chinese Twitter Clone Site - 999 views
SourceForge Unblocked in China - 909 views
Boycott China Product If You Really Love China - 898 views
YouTube Blocked in China Again - 841 views
Custom WordPress Database Error Page - 838 views
DB2ASP - Free Access Database to ASP Converter - 812 views
All in all it was a fairly busy but very satisfying year of blogging here at Moonlight Blog. Thanks to the many readers who have contributed either with guest posts, comments, emails and tip offs. I’m looking forward to yet another great year in 2009.
All in all it was a fairly busy but very satisfying year of blogging here at Moonlight Blog. Thanks to the many readers who have contributed either with guest posts, comments, emails and tip offs. I’m looking forward to yet another great year in 2009.
Thursday, December 25, 2008
Security Risks in GoDaddy Total DNS Control
Web server authentication is an essential element of an organization's trust strategy for e-business. By reliably authenticating web servers to visiting browsers, SSL server certificates help build that trust.
Until recently, GoDaddy, the world's largest ICANN-accredited domain registrar, have been found a security risk in there Total DNS Control panel. GoDaddy Total DNS Control allows user to perform advanced DNS functions, such as changing zone records. But the latest revision of TDNS is not safe, because they even the use of http access to the Total DNS Control, This is really terrible. As we know http(Hypertext Transfer Protocol) is extremely unsafe. The others can use Sniffer to intercept, view and analyze all of the HTTP traffic between a web browser or any program that uses the HTTP protocol and the web server. Given these factors, many organizations would prefer to manage web server authentication with the RSA Web Server SSL technology application.
Hypertext Transfer Protocol Secure (HTTPS) is a combination of the Hypertext Transfer Protocol and a network security protocol.HTTPS has also been known as "Hypertext Transfer Protocol over Secure Socket Layer"(SSL). An SSL Certificate enables encryption of sensitive information during online transactions. Each SSL Certificate contains unique, authenticated information about the certificate owner. A Certificate Authority verifies the identity of the certificate owner when it is issued.
To fix that security risks in GoDaddy, remember: If you use GoDaddy's Total DNS Control Panel, do not click on the original link to "Total DNS Control and MX Records", that link is unsafe http protocol. To invoke HTTPS, replaces "http://" with "https://" in the Web address. The link is such like this:
https://tdns.secureserver.net/?domain=YourDomainName&prog_id=GoDaddy&type=1
Until recently, GoDaddy, the world's largest ICANN-accredited domain registrar, have been found a security risk in there Total DNS Control panel. GoDaddy Total DNS Control allows user to perform advanced DNS functions, such as changing zone records. But the latest revision of TDNS is not safe, because they even the use of http access to the Total DNS Control, This is really terrible. As we know http(Hypertext Transfer Protocol) is extremely unsafe. The others can use Sniffer to intercept, view and analyze all of the HTTP traffic between a web browser or any program that uses the HTTP protocol and the web server. Given these factors, many organizations would prefer to manage web server authentication with the RSA Web Server SSL technology application.
Hypertext Transfer Protocol Secure (HTTPS) is a combination of the Hypertext Transfer Protocol and a network security protocol.HTTPS has also been known as "Hypertext Transfer Protocol over Secure Socket Layer"(SSL). An SSL Certificate enables encryption of sensitive information during online transactions. Each SSL Certificate contains unique, authenticated information about the certificate owner. A Certificate Authority verifies the identity of the certificate owner when it is issued.
To fix that security risks in GoDaddy, remember: If you use GoDaddy's Total DNS Control Panel, do not click on the original link to "Total DNS Control and MX Records", that link is unsafe http protocol. To invoke HTTPS, replaces "http://" with "https://" in the Web address. The link is such like this:
https://tdns.secureserver.net/?domain=YourDomainName&prog_id=GoDaddy&type=1
Sunday, December 14, 2008
Top Ten Best Video Games of 2008
In a year when most businesses tried to figure out how to stay alive, the video game industry thrived thanks to two things: great games, and you. So give yourself a pat on the back; your thirst for single-handedly saving the world with magic, guns, and fast thumbs has kept the gaming industry going strong when all else seems to be going wrong.
Of all the games that Time Magazine has reviewed so far this year, 10 games have a tremendous amount of momentum going into the awards.
1. Grand Theft Auto IV
It's ironic that GTA became a football in the debate over sex and violence in video games, because where it belongs is in the debate over whether video games count as art. No game developers are more radical and more passionate about the storytelling power of their medium than folks at Rockstar North, and GTA IV is the company's most ambitious work ever. It's the story of Niko Bellic, an Eastern European soldier-for-hire fighting his way up the organized crime ladder in an archly satirical version of New Yo— I mean, Liberty City. It's a grade-A shoot-'em-up that doubles as an interactive novel and triples as a sly critique of American consumer culture.
2. Braid
Of all the game genres to make a comeback this year, who would've picked the side-scrolling platformer? At first blush Braid looks like a standard old-school Super Mario Bros.-style game. But there's a twist: on top of standard game mechanics like running and jumping, Braid adds the ability to manipulate time: if you make a mistake you can wind back the clock and try again. It sounds simple, but as Portal proved last year, a simple mechanic in the hands of a brilliant developer can yield near-infinite entertainment.
3. LittleBigPlanet
The hero of LittleBigPlanet is a tiny person made out of some kind of coarse-textured fabric. His name is Sackboy. Like everything else in his world, he is a toy. He runs and jumps and slides through an endlessly inventive landscape made of cushions and weights and ramps and springs and glowing bubbles, all rendered with a gritty, high-res perfection which finally shows you why that PS3 you bought was so expensive. Nobody shoots at anybody. When you're done with the levels the game comes with — and that takes a long time — you can build and download more. LittleBigPlanet is not an adrenaline game; it's a restful, chill-out kind of experience. Let Sackboy do all the work. You have all the fun.
4. Rock Band 2
Hands down the best party game ever made, Rock Band 2 does what the first Rock Band did — simulate the experience of singing and playing drums, guitar or bass in an actual rock band — only better, faster, harder and with more songs to choose from. The key is Rock Band 2's candy-colored interface, which is so clear and intuitive that it feels like there's nothing standing between you and the music. Boot up, jack in, and rock out.
5. Gears of War 2
After all that time Marcus Fenix spent in Gears of War sawing Locusts in half the long way, you'd think he would have moved on to some less stressful activity like playing LittleBigPlanet. Actually not. Except for some new multiplayer modes, Gears of War 2 is remarkably similar to the first installment: lots of shooting and duck-and-covering and, yes, sawing, plus the usual hard-boiled gravelly-voiced dialogue. Not that this is in any way a problem. The main difference is that the backgrounds all this action happens in front of are now even more spectacular: ruined churches, soaring caverns, jagged mountains, airships made out of giant bugs. Sera never looked so good — maybe when Marcus is done killing Locusts he can finally retire there.
6. Dead Space
The hero of Dead Space obviously never saw Alien, or he'd know not to answer distress signals from remote mining spaceships. Turns out the ship has been taken over by an evil and really gross alien menace that turns human corpses into horrible deformed zombies. Your job is to figure out what happened and fix it and not die while doing so. Dead Space doesn't break new ground, it's just bloody, scary survival horror at its finest — cool weapons, amazing environments, fast action, fantastic zero-G combat, no letup, no mercy.
7. Star Wars: The Force Unleashed
Evil Jedi walks into a room. Room is full of anonymous Stormtroopers, Jawas, rancors, etc. Does he (a) shock them to death with Force Lightning, (b) grab them with the Force and throw them against the walls and each other till they die, (c) kill them with a sweet light saber combo, (d) pull a passing TIE fighter out of the sky and smash it into them...I could go on. This game has flaws, but it's so unbelievably satisfying to cut loose with the Force, Jedi honor be damned, that the flaws don't really register. This is Star Wars without any Ewokkish sentimentality, and it's the best thing to happen to the franchise in years.
8. Hunted Forever
The future is a terrible place, but at least it's pretty stylin' — it looks like an animated title sequence from a 1960s movie, all angular graphics and silhouettes and primary colors. You're a tiny running man sprinting, jumping and sliding through a post-apocalyptic landscape, relentlessly pursued by an enormous hovering robot. This is a free Flash game, and it's on this list both for its own merits and as a representative of all the beautiful, quirky Flash games that came out this year. Flash developers don't have $20 million budgets on the line when they make a game, which means they can take risks and try anything.
9. Fieldrunners
Fun fact: back in the 1970s, before they founded Apple, Steve Jobs and Steve Wozniak helped create the original game of Breakout for Atari. But Apple has never really shown much fight when it comes to the gaming market. Now it doesn't have to. With the opening of the App Store and the release of development tools, third-party developers have converted the iPhone and the iPod Touch into handheld gaming devices that will soon be serious competition for the Nintendo DS and Sony's PSP. The pick of the first litter is Fieldrunners, a fast and furious tower defense game that looks great on those super-bright, super-crisp screens and seamlessly integrates the famous touchscreen as a game controller.
10. Spore
Sims creator Will Wright spent seven years writing, researching and designing this evolutionary epic, which may well be the most ambitious game ever made. Spore follows the history of a single species, designed by you, from a cute little single cell up through sentience, civilization and finally space exploration. The innovation here doesn't lie in the gameplay, which is merely entertaining, but in the sophistication of the animations that make your creation walk and move and dance, and in the game's hubristic, near-infinite scope.
Source: http://www.time.com/
Of all the games that Time Magazine has reviewed so far this year, 10 games have a tremendous amount of momentum going into the awards.
1. Grand Theft Auto IV
It's ironic that GTA became a football in the debate over sex and violence in video games, because where it belongs is in the debate over whether video games count as art. No game developers are more radical and more passionate about the storytelling power of their medium than folks at Rockstar North, and GTA IV is the company's most ambitious work ever. It's the story of Niko Bellic, an Eastern European soldier-for-hire fighting his way up the organized crime ladder in an archly satirical version of New Yo— I mean, Liberty City. It's a grade-A shoot-'em-up that doubles as an interactive novel and triples as a sly critique of American consumer culture.
2. Braid
Of all the game genres to make a comeback this year, who would've picked the side-scrolling platformer? At first blush Braid looks like a standard old-school Super Mario Bros.-style game. But there's a twist: on top of standard game mechanics like running and jumping, Braid adds the ability to manipulate time: if you make a mistake you can wind back the clock and try again. It sounds simple, but as Portal proved last year, a simple mechanic in the hands of a brilliant developer can yield near-infinite entertainment.
3. LittleBigPlanet
The hero of LittleBigPlanet is a tiny person made out of some kind of coarse-textured fabric. His name is Sackboy. Like everything else in his world, he is a toy. He runs and jumps and slides through an endlessly inventive landscape made of cushions and weights and ramps and springs and glowing bubbles, all rendered with a gritty, high-res perfection which finally shows you why that PS3 you bought was so expensive. Nobody shoots at anybody. When you're done with the levels the game comes with — and that takes a long time — you can build and download more. LittleBigPlanet is not an adrenaline game; it's a restful, chill-out kind of experience. Let Sackboy do all the work. You have all the fun.
4. Rock Band 2
Hands down the best party game ever made, Rock Band 2 does what the first Rock Band did — simulate the experience of singing and playing drums, guitar or bass in an actual rock band — only better, faster, harder and with more songs to choose from. The key is Rock Band 2's candy-colored interface, which is so clear and intuitive that it feels like there's nothing standing between you and the music. Boot up, jack in, and rock out.
5. Gears of War 2
After all that time Marcus Fenix spent in Gears of War sawing Locusts in half the long way, you'd think he would have moved on to some less stressful activity like playing LittleBigPlanet. Actually not. Except for some new multiplayer modes, Gears of War 2 is remarkably similar to the first installment: lots of shooting and duck-and-covering and, yes, sawing, plus the usual hard-boiled gravelly-voiced dialogue. Not that this is in any way a problem. The main difference is that the backgrounds all this action happens in front of are now even more spectacular: ruined churches, soaring caverns, jagged mountains, airships made out of giant bugs. Sera never looked so good — maybe when Marcus is done killing Locusts he can finally retire there.
6. Dead Space
The hero of Dead Space obviously never saw Alien, or he'd know not to answer distress signals from remote mining spaceships. Turns out the ship has been taken over by an evil and really gross alien menace that turns human corpses into horrible deformed zombies. Your job is to figure out what happened and fix it and not die while doing so. Dead Space doesn't break new ground, it's just bloody, scary survival horror at its finest — cool weapons, amazing environments, fast action, fantastic zero-G combat, no letup, no mercy.
7. Star Wars: The Force Unleashed
Evil Jedi walks into a room. Room is full of anonymous Stormtroopers, Jawas, rancors, etc. Does he (a) shock them to death with Force Lightning, (b) grab them with the Force and throw them against the walls and each other till they die, (c) kill them with a sweet light saber combo, (d) pull a passing TIE fighter out of the sky and smash it into them...I could go on. This game has flaws, but it's so unbelievably satisfying to cut loose with the Force, Jedi honor be damned, that the flaws don't really register. This is Star Wars without any Ewokkish sentimentality, and it's the best thing to happen to the franchise in years.
8. Hunted Forever
The future is a terrible place, but at least it's pretty stylin' — it looks like an animated title sequence from a 1960s movie, all angular graphics and silhouettes and primary colors. You're a tiny running man sprinting, jumping and sliding through a post-apocalyptic landscape, relentlessly pursued by an enormous hovering robot. This is a free Flash game, and it's on this list both for its own merits and as a representative of all the beautiful, quirky Flash games that came out this year. Flash developers don't have $20 million budgets on the line when they make a game, which means they can take risks and try anything.
9. Fieldrunners
Fun fact: back in the 1970s, before they founded Apple, Steve Jobs and Steve Wozniak helped create the original game of Breakout for Atari. But Apple has never really shown much fight when it comes to the gaming market. Now it doesn't have to. With the opening of the App Store and the release of development tools, third-party developers have converted the iPhone and the iPod Touch into handheld gaming devices that will soon be serious competition for the Nintendo DS and Sony's PSP. The pick of the first litter is Fieldrunners, a fast and furious tower defense game that looks great on those super-bright, super-crisp screens and seamlessly integrates the famous touchscreen as a game controller.
10. Spore
Sims creator Will Wright spent seven years writing, researching and designing this evolutionary epic, which may well be the most ambitious game ever made. Spore follows the history of a single species, designed by you, from a cute little single cell up through sentience, civilization and finally space exploration. The innovation here doesn't lie in the gameplay, which is merely entertaining, but in the sophistication of the animations that make your creation walk and move and dance, and in the game's hubristic, near-infinite scope.
Source: http://www.time.com/
Wednesday, December 10, 2008
Wordpress 2.7 Released
Wordpress 2.7 has been officially released and is available for download. There are many new features added in 2.7 and the first thing you will notice is the re-designed user interface and Dashboard.
Version 2.7 should be a major upgrade into the WordPress software. Here are some of the changes that it brings:
The most exciting stuff is the automatic upgrade. From now when new versions get released all you will have to do is one click, and the software will take care of the rest. I am sure this will make WordPress a much more secure software, too.
Version 2.7 should be a major upgrade into the WordPress software. Here are some of the changes that it brings:
- new interface to make it easier to perform the admin tasks
- customization options on the admin screens
- the ability to reply to comments from the dashboard
- embed support for comments threading
- drag and drop support on some sections
The most exciting stuff is the automatic upgrade. From now when new versions get released all you will have to do is one click, and the software will take care of the rest. I am sure this will make WordPress a much more secure software, too.
Monday, December 1, 2008
Pownce is Shutting Down
Microblogging service Pownce, is closing down on December 15. As of today, Pownce will no longer be accepting new users or new pro accounts. The Pownce team has joined SixApart.
Pownce have built an export tool so users can save the content. Users can find the export tool at Settings > Export. Please export content by December 15, 2008, as the site will not be accessible after this date.
Pownce have built an export tool so users can save the content. Users can find the export tool at Settings > Export. Please export content by December 15, 2008, as the site will not be accessible after this date.
Saturday, November 29, 2008
Top Ten Wordpress Security Tips
Below are 10 security tips that you can easily implement on your WordPress blog. Please share one or more life-savers you use permanently to help protect yourself from WordPress security issues.
1. Upgrade Wordpress - In general, keeping your Wordpress installation up to date is a great way to avoid known problems. Do note that the lastest version, especially in the case of major upgrades, may cause more problems then it resolves.
2. WordPress Version - The tag in your header.php that displays your current version of wordpress. Since everyone knows your wordpress version this way, your blog is prone to hackers if you have not upgraded to the new version.
3. WordPress Username - Every hacker knows Wordpress has a user “admin” with god-like administration privileges. Slow the hackers down by removing the “admin” user. Create a Wordpress user with admin privileges using the administration interface. Log out of Wordpress and log back in with the new user. Delete the admin user. The new admin user should be different than your normal post author.
4. WordPress Password - Are you still logging into your wp-admin page with the same default password that was emailed to you? If so, CHANGE IT! That password is only 6 characters and just numbers and letters. Make it complex and more than 10 characters if you can. Also, try not to use words, make it a nice jumble of letters, numbers, and symbols.
5. Prevent Directory Listing - In many Wordpress installations it is possible to view a list of installed plugins by navigating to the /wp-content/plugins/ directory. This is not a good idea as known plugin vulnerabilities can than be easily exploited. Add an empty default index file, such as index.html, to the directory. You can also protect it using an .htaccess file assuming you're using Apache.
6. Protect Your WP-Admin Folder - You can protect your Wordpress admin folder by allowing access to it from a defined set of IP addresses. Everything else will bring up a Forbidden error message. So if you only access your blog from one or two places routinely, it’s worth implementing. Also, you’re supposed to create a new .htaccess file inside your wp-admin folder, not replace the one at the root of your blog.
7. Protect From Search Engines - There is no need to have all of your filesWordpress files indexed by Google, so it’s best to block them in your robots.txt file. Add the following line to your list:Disallow: /wp-*
8. Install Login Lockdown WordPress Plugin - This plugin records the IP address and timestamp of every failed WordPress login attempt. If more than a certain number of attempts are detected within a short period of time from the same IP range, then the login function is disabled for all requests from that range.
9. Install WordPress Database Backup Plugin - You always have to take regular backups of your file directories as well as the database. WordPress Database Backup plugin creates backups of your core WordPress tables as well as other tables of your choice in the same database.
10. Install Wordpress Security Scan Plugin - The WP Security Scan plugin attempts to both to audit your blog security and to implement many of the suggestions mentioned above.
1. Upgrade Wordpress - In general, keeping your Wordpress installation up to date is a great way to avoid known problems. Do note that the lastest version, especially in the case of major upgrades, may cause more problems then it resolves.
2. WordPress Version - The tag in your header.php that displays your current version of wordpress. Since everyone knows your wordpress version this way, your blog is prone to hackers if you have not upgraded to the new version.
3. WordPress Username - Every hacker knows Wordpress has a user “admin” with god-like administration privileges. Slow the hackers down by removing the “admin” user. Create a Wordpress user with admin privileges using the administration interface. Log out of Wordpress and log back in with the new user. Delete the admin user. The new admin user should be different than your normal post author.
4. WordPress Password - Are you still logging into your wp-admin page with the same default password that was emailed to you? If so, CHANGE IT! That password is only 6 characters and just numbers and letters. Make it complex and more than 10 characters if you can. Also, try not to use words, make it a nice jumble of letters, numbers, and symbols.
5. Prevent Directory Listing - In many Wordpress installations it is possible to view a list of installed plugins by navigating to the /wp-content/plugins/ directory. This is not a good idea as known plugin vulnerabilities can than be easily exploited. Add an empty default index file, such as index.html, to the directory. You can also protect it using an .htaccess file assuming you're using Apache.
6. Protect Your WP-Admin Folder - You can protect your Wordpress admin folder by allowing access to it from a defined set of IP addresses. Everything else will bring up a Forbidden error message. So if you only access your blog from one or two places routinely, it’s worth implementing. Also, you’re supposed to create a new .htaccess file inside your wp-admin folder, not replace the one at the root of your blog.
7. Protect From Search Engines - There is no need to have all of your filesWordpress files indexed by Google, so it’s best to block them in your robots.txt file. Add the following line to your list:Disallow: /wp-*
8. Install Login Lockdown WordPress Plugin - This plugin records the IP address and timestamp of every failed WordPress login attempt. If more than a certain number of attempts are detected within a short period of time from the same IP range, then the login function is disabled for all requests from that range.
9. Install WordPress Database Backup Plugin - You always have to take regular backups of your file directories as well as the database. WordPress Database Backup plugin creates backups of your core WordPress tables as well as other tables of your choice in the same database.
10. Install Wordpress Security Scan Plugin - The WP Security Scan plugin attempts to both to audit your blog security and to implement many of the suggestions mentioned above.
Tuesday, November 25, 2008
Disable WordPress Autosave Plugin
WordPress autosave is the best features which I hate in WordPress. AutoSave will auto save a copy of edited post or page every 60 seconds provided there is a change on the content in the editor. However, there is only ever a maximum of one AutoSave version for any given post. New AutoSaves created will overwrite old AutoSaves. Beside, AutoSaves are stored as a special type of revision so that the auto saved with a more recent version of data does not overwrite actual published content, and is used to restore unsaved work only when necessary.
While each Post Revisions is stored in its own database table, the auto-save is only stored once with previous versions being overwritten by the new auto-saved content. So, if you’re worried about your database growing to massive proportions because of auto-save, you can stop worrying.
These are methods that disable or delay the WordPress autosave functions. The Most easy way is using plugin. The disabling plugin works with versions 2.3 through 2.7 while the delay configuration works with 2.5 and later.
Copy this text to a text file, name it whatever you want (using the .php extension, of course) and upload it to your WordPress plugin directory. Activate it and it works immediately, but you need to clear your browser cache:
While each Post Revisions is stored in its own database table, the auto-save is only stored once with previous versions being overwritten by the new auto-saved content. So, if you’re worried about your database growing to massive proportions because of auto-save, you can stop worrying.
These are methods that disable or delay the WordPress autosave functions. The Most easy way is using plugin. The disabling plugin works with versions 2.3 through 2.7 while the delay configuration works with 2.5 and later.
Copy this text to a text file, name it whatever you want (using the .php extension, of course) and upload it to your WordPress plugin directory. Activate it and it works immediately, but you need to clear your browser cache:
<?php
/*
Plugin Name: Disable autosave
*/
add_action('admin_print_scripts', 'plugin_deregister_autosave');
function plugin_deregister_autosave() {
wp_deregister_script('autosave');
}
define('WP_POST_REVISIONS',false);
?>
Sunday, November 23, 2008
Z-Blog URL Redirect Security Affected Spam Attacks
Z-Blog system contain a security issue that allows spam attack to Wikipedia by using url redirect.
The design of Z-Blog anti-spam encrypts the URL before redirect it. The name of the redirected file is c_urlredirect.asp. With the parameter of this page Z-Blog kann redirect to various pages. Sorrowfully the used encryption is very simple. One just need to put the odd characters together. With this methode blackhat SEO manipulates redirects from other Z-Blog websites to call its own website. Thus even if the original address is listed on the blacklist by Wikipedia, the manipulated redirect would still work and be used as spam.
The solution for this problem is not easy. The most simple way is to delete c_urlredirect.asp. But this method would also prevent the blogger himself make redirects.
Source . thanks for Wing translation
The design of Z-Blog anti-spam encrypts the URL before redirect it. The name of the redirected file is c_urlredirect.asp. With the parameter of this page Z-Blog kann redirect to various pages. Sorrowfully the used encryption is very simple. One just need to put the odd characters together. With this methode blackhat SEO manipulates redirects from other Z-Blog websites to call its own website. Thus even if the original address is listed on the blacklist by Wikipedia, the manipulated redirect would still work and be used as spam.
The solution for this problem is not easy. The most simple way is to delete c_urlredirect.asp. But this method would also prevent the blogger himself make redirects.
Source . thanks for Wing translation
Saturday, November 22, 2008
Google Earth Layer Blocked in China
China appears to have blocked access to the popular internet maps service - Google Earth. Google Earth is a virtual globe program that displays satellite images of varying resolution of the Earth's surface, allowing users to visually see things like cities and houses from a bird's eye view.
Google's map and satellite-photo service offered Chinese Internet users something they rarely could see: a bird's-eye view of the secret compound of Zhongnanhai(located west of the Forbidden City), where the country's top leaders live and work.
But in recent weeks, some layer of Google Earth(such as Google Earth Community) could not load and work in China. The Google Earth Community is an online forum which is dedicated to producing placemarks of interesting or educational perspectives. It may be found on the Google Earth webpage or under the Help section on the program itself. After downloading a placemark, it will automatically run Google Earth (if not opened), and fly to the area specified by the person who placed it. Once there, you can add it to your "My Places" by right clicking on the icon and selecting "Save to My Places". Additionally, anyone can post a placemark for others to download; as long as you have an account.
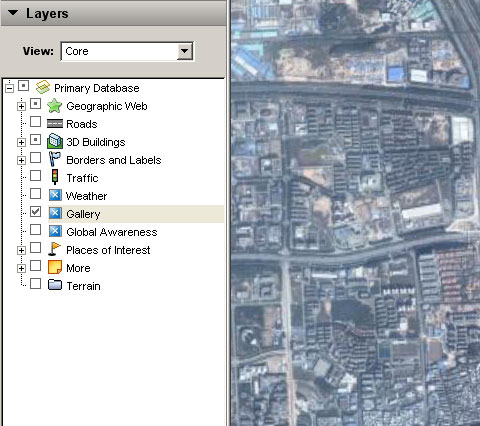
When I run a proxy program, and open Google Earth again, the Google Earth Community layer is right there, everything is ok.
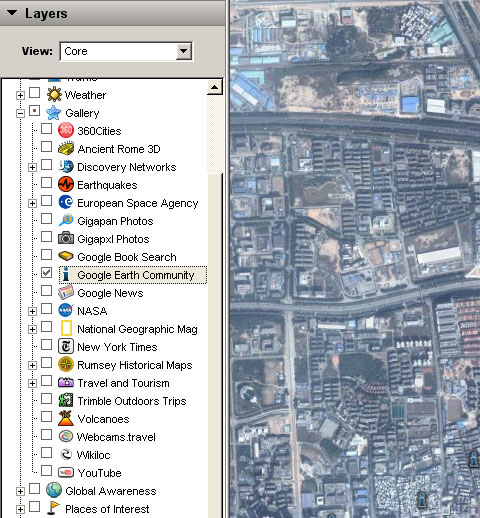
Then I close the proxy program and click the layer again, it's tell me "Fetch of NetworkLink failed(http://mw1.google.com/): Connect Failed."
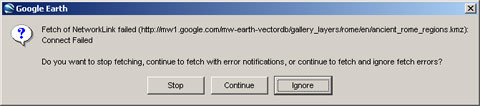
That mean the Weather,Gallery and Global Awareness layer is blocked in China. Google Earth Community is in the Gallery layer, so it cannot be open again.
If the Chinese government is blocking its own citizens from seeing where their leaders live, whereas the rest of the world can see just fine, we're talking some major institutional paranoia.
Google's map and satellite-photo service offered Chinese Internet users something they rarely could see: a bird's-eye view of the secret compound of Zhongnanhai(located west of the Forbidden City), where the country's top leaders live and work.
But in recent weeks, some layer of Google Earth(such as Google Earth Community) could not load and work in China. The Google Earth Community is an online forum which is dedicated to producing placemarks of interesting or educational perspectives. It may be found on the Google Earth webpage or under the Help section on the program itself. After downloading a placemark, it will automatically run Google Earth (if not opened), and fly to the area specified by the person who placed it. Once there, you can add it to your "My Places" by right clicking on the icon and selecting "Save to My Places". Additionally, anyone can post a placemark for others to download; as long as you have an account.

When I run a proxy program, and open Google Earth again, the Google Earth Community layer is right there, everything is ok.

Then I close the proxy program and click the layer again, it's tell me "Fetch of NetworkLink failed(http://mw1.google.com/): Connect Failed."

That mean the Weather,Gallery and Global Awareness layer is blocked in China. Google Earth Community is in the Gallery layer, so it cannot be open again.
If the Chinese government is blocking its own citizens from seeing where their leaders live, whereas the rest of the world can see just fine, we're talking some major institutional paranoia.
Thursday, October 30, 2008
Is Blog Dead in China ?
In the past year, there is a continuing discussion in the Chinese blogosphere on whether blog culture is dying down. Moreover, recently bokee.com and blogchina.com, the two earliest BSPs founded by Fang dong-xing in China, are at business crisis. Fang is looking for investing to transform the websites into multi-media community platform.
What we see is: BSP and services related with blogs are slowly disappearing, blog has passed its golden days and walked into a dark future. The main reason is because the services around blogs cannot make a profit.
Why can't they make a profit? The content quality of blog is better than SNS, Twitter and Digg, their traffics are high. They should be able to get income from Ads. However, at present, blogger's income is too narrowed. Basically, they depends on Google AdSense. Which means their profit is affected by Google.
When Google entered the scene, it developed a huge number of blogging tools, such as google reader, feedburner, blogsearch, etc… which destroyed other BSPs dream for profit while google has a monopoly status in the market.
Blog is more open and individualized, its content quality is relative higher. SNS is more closed, especially towards search engine. It contrasts with blog's openness and affects information dissemination. A good article is very difficult to get disseminated via SNS. Now most of the SNS in China are coping the facebook, which is a dead end. The best SNS is Tencent's QQ, but you can't find any similarity between QQ and facebook. The funny thing is Tencent never claimed itself to be a SNS.
Thanks globalvoicesonline translation
What we see is: BSP and services related with blogs are slowly disappearing, blog has passed its golden days and walked into a dark future. The main reason is because the services around blogs cannot make a profit.
Why can't they make a profit? The content quality of blog is better than SNS, Twitter and Digg, their traffics are high. They should be able to get income from Ads. However, at present, blogger's income is too narrowed. Basically, they depends on Google AdSense. Which means their profit is affected by Google.
When Google entered the scene, it developed a huge number of blogging tools, such as google reader, feedburner, blogsearch, etc… which destroyed other BSPs dream for profit while google has a monopoly status in the market.
Blog is more open and individualized, its content quality is relative higher. SNS is more closed, especially towards search engine. It contrasts with blog's openness and affects information dissemination. A good article is very difficult to get disseminated via SNS. Now most of the SNS in China are coping the facebook, which is a dead end. The best SNS is Tencent's QQ, but you can't find any similarity between QQ and facebook. The funny thing is Tencent never claimed itself to be a SNS.
Thanks globalvoicesonline translation
GoDaddy and SourceForge Blocked in China Again
GoDaddy, the world's largest ICANN-accredited domain registrar, and SourceForge, the world's largest development and download repository of Open Source code and applications, appears to blocked in Mainland China again after Beijing 2008 Olympic Games closed.
A screen copy of the command tracert shows that the problem is a router inside China Telecom.
Update: SourceForge unblocked on Nov 2 2008, GoDaddy unblocked on Nov 10 2008.
A screen copy of the command tracert shows that the problem is a router inside China Telecom.
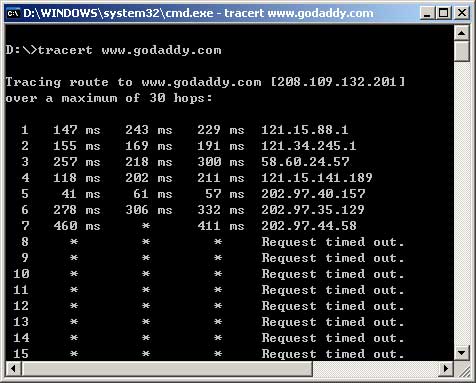

Update: SourceForge unblocked on Nov 2 2008, GoDaddy unblocked on Nov 10 2008.
Friday, October 24, 2008
China Internet Censorship After Olympic Games
As Beijing 2008 Olympic Games closed, the Internet censorship in China further tightened. Undeniably, this deterioration has affected and frustrated an increasing number of netizens in China.
lot's of foreign websites have been blocked again after the Beijing Olympics drew to an end. Meanwhile, although other foreign websites remain approachable in China, some of their touchy contents are actually not accessible.
lot's of foreign websites have been blocked again after the Beijing Olympics drew to an end. Meanwhile, although other foreign websites remain approachable in China, some of their touchy contents are actually not accessible.
Wednesday, October 8, 2008
Want China Milk, Mr. Mandelson?
British politician Peter Mandelson, who was feted in China for drinking a glass of yoghurt on television in Beijing last week, has been rushed to hospital suffering from a kidney stone.
EU Trade Commissioner Peter Mandelson drinks a Beijing-branded yogurt at a press conference in the Chinese capital on Friday September 26, 2008. Mandelson said he was confident of Chinese dairy products despite the recent tainted milk scandal. On October 6, Peter Mandelson is to have a kidney stone removed after attending the first meeting of Gordon Brown's economic war council.
Thousands of babies across China have suffered kidney stones after drinking formula milk mixed with the industrial plastic melamine.
Also, if you want to get an idea of how the Chinese government is handling the post-scandal media since the milk powder contamination was revealed, here are instructions reportedly from the propaganda bureau on how to report the incident:
EU Trade Commissioner Peter Mandelson drinks a Beijing-branded yogurt at a press conference in the Chinese capital on Friday September 26, 2008. Mandelson said he was confident of Chinese dairy products despite the recent tainted milk scandal. On October 6, Peter Mandelson is to have a kidney stone removed after attending the first meeting of Gordon Brown's economic war council.
Thousands of babies across China have suffered kidney stones after drinking formula milk mixed with the industrial plastic melamine.
Also, if you want to get an idea of how the Chinese government is handling the post-scandal media since the milk powder contamination was revealed, here are instructions reportedly from the propaganda bureau on how to report the incident:
Recently, the Sanlu mild powder contamination story attracted a lot of attention on the Internet. Now we are issuing some requirements for managing online news publishing:
1. Strictly standardize news sources, only use dispatches from Xinhua, People’s Daily and other central media outlets.
2. Do not make any headlines or features on this topic. Emphasize the government’s handling of the crisis and progress, and the care given to the babies by hospitals and other care providers.
3. Forums and blogs should not recommend this topic, not put it on the top of their pages, and the atmosphere and number of threads in the forums should be monitored and controlled.
4. Firmly block and delete information and posts that criticize the Party, the government, instigate petitioning and spread rumors.
5. Mobilize online commentators to guide the opinions. The general guidance should be based on information released by the Ministry of Health, and lead online users to support the Party and the government, convey the effectiveness of the efforts by concerned agencies.
Tuesday, September 30, 2008
Godaddy Promo Code Expired
Today when I purchase of domain names in GoDaddy, I found that the Godaddy Promo Codes of 6.95 $ discount code have been expired, I can not continue to use the 6.95 coupons code. While I input that code, it will become $ 7.49 U.S. dollars, an increase of 0.5 U.S. dollars, I tested the four promo codes, all become 7.49 U.S. dollars. Do not know why, probably GoDaddy want the customers to spend more money to buy the domain name, the U.S. economic downturn, ah.
Saturday, September 20, 2008
MSN and Gtalk Local Password Hacking
I have to tell the true that local password of MSN & GTalk can be easily hacked. You can even find the local password directly by using a hack tool named MessenPass. This means it is high risky if you save the password of MSN or GTalk in the local PC.
MessenPass can be used to get the passwords for the current logged-on user on your local computer, and it works if you chose the remember your password in one of the above programs.
Password hashing is a way of encrypting a password before it's stored so that if local computer gets into the wrong hands, the damage is limited. Hashing is nothing new - it's been in use in Unix system password files since long before my time, and quite probably in other systems long before that.
A hash (also called a hash code, digest, or message digest) can be thought of as the digital fingerprint of a piece of data. You can easily generate a fixed length hash for any text string using a one-way mathematical process. It is next to impossible to (efficiently) recover the original text from a hash alone. It is also vastly unlikely that any different text string will give you an identical hash - a 'hash collision'. These properties make hashes ideally suited for storing your application's passwords. Why? Because although an attacker may compromise a part of your system and reveal your list of password hashes, they can't determine from the hashes alone what the real passwords are.
We've established that it's incredibly difficult to recover the original password from a hash, so how will the application know if a user has entered the correct password or not? Quite simply - by generating a hash of the user-supplied password and comparing this 'fingerprint' with the hash stored in your user profile, you'll know whether or not the passwords match.
MessenPass can be used to get the passwords for the current logged-on user on your local computer, and it works if you chose the remember your password in one of the above programs.
Password hashing is a way of encrypting a password before it's stored so that if local computer gets into the wrong hands, the damage is limited. Hashing is nothing new - it's been in use in Unix system password files since long before my time, and quite probably in other systems long before that.
A hash (also called a hash code, digest, or message digest) can be thought of as the digital fingerprint of a piece of data. You can easily generate a fixed length hash for any text string using a one-way mathematical process. It is next to impossible to (efficiently) recover the original text from a hash alone. It is also vastly unlikely that any different text string will give you an identical hash - a 'hash collision'. These properties make hashes ideally suited for storing your application's passwords. Why? Because although an attacker may compromise a part of your system and reveal your list of password hashes, they can't determine from the hashes alone what the real passwords are.
We've established that it's incredibly difficult to recover the original password from a hash, so how will the application know if a user has entered the correct password or not? Quite simply - by generating a hash of the user-supplied password and comparing this 'fingerprint' with the hash stored in your user profile, you'll know whether or not the passwords match.
Subscribe to:
Comments (Atom)